Multimedia content
- Images (2)
- TrueConf introduces a new solution to protect on-premises video collaboration systems from external threats at GITEX Africa 2023 (1)
- TrueConf introduces a new solution to protect on-premises video collaboration systems from external threats at GITEX Africa 2023 (2)
- All (2)
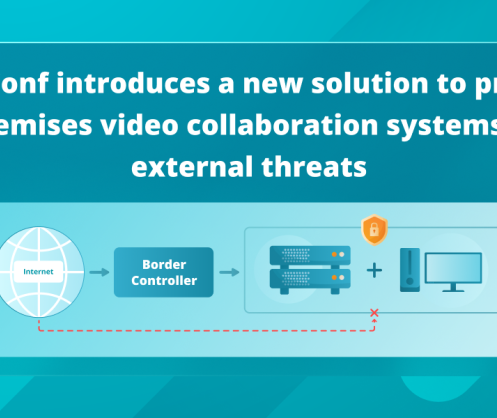
TrueConf introduces a new solution to protect on-premises video collaboration systems from external threats at GITEX Africa 2023
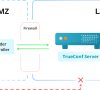
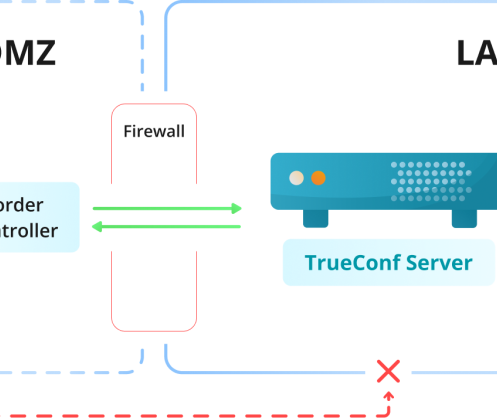
With TrueConf Border Controller, IT departments can hide a real IP address of TrueConf Server deployed in a private network
With TrueConf Border Controller, it is possible to additionally encrypt data transmitted via the Internet with subsequent decryption on each separate TrueConf Server instance
TrueConf, an award-winning video conferencing developer, introduces a new security-focused technology at GITEX Africa 2023 (https://GITEXAfrica.com/), one of the largest tech & startup events that took place in Morocco on May 31 — June 2 2023. TrueConf Border Controller is a software solution that hides IP addresses of TrueConf on-premises team collaboration platforms, blocks unwanted connections of external users, and provides additional protection against DDoS attacks.
Communications within large enterprises and government organizations are becoming increasingly exposed to data breaches, cyber attacks, and other security threats that can compromise sensitive information. According to Cloudflare, in the last quarter of 2022, the amount of DDoS attack traffic increased by 79%. Such attacks constituted 35% of all traffic to Aviation and Aerospace Internet properties, and over a third of all traffic to the Finance industries.
In response to strong demand for enterprise IT security, TrueConf developed TrueConf Border Controller, a software solution that safeguards self-hosted team collaboration systems against potential external network threats. With TrueConf Border Controller, IT departments can hide a real IP address of TrueConf Server deployed in a private network.
The solution protects on-premises video conferencing platforms from unwanted external connections. It is achieved thanks to the protocol verification algorithm that allows external users to connect to TrueConf Server via the secure proprietary protocol used by TrueConf client applications for Windows, Linux, macOS, iOS, and Android. If any third-party protocol is used, the connection will not be established.
Border Controller is a valuable addition for organizations that use federated TrueConf Server instances. Federation allows users registered on independent TrueConf Server platforms to communicate with each other. With TrueConf Border Controller, it is possible to additionally encrypt data transmitted via the Internet with subsequent decryption on each separate TrueConf Server instance.
In case attackers try to send multiple connection requests via third-party protocols to conduct an attack, their attempts will be immediately blocked by TrueConf Border Controller. In its turn, TrueConf Server will remain invulnerable and continue its stable and secure operation in the private network, and its IP address will not be revealed even if TrueConf Border Controller is damaged. The company can also set up backup Border Controllers with other external IP addresses, which will be activated if the primary one is inaccessible.
Distributed by APO Group on behalf of GITEX Africa.
For more information, please contact:
Dmitry Odintsov
TrueConf’s CEO
Phone: +1 (833) 878-32-63
Email: pr@trueconf.com
About TrueConf:
TrueConf equips desktops, mobiles, and meeting rooms with award-winning video collaboration capabilities and provides businesses worldwide with exceptional meeting experiences. TrueConf apps and solutions are easy to use and are fully compatible with legacy SIP/H.323 equipment, enabling customers to save money on infrastructure while still utilizing state-of-the art technologies such as scalable video coding (SVC) and intelligent stream manipulation. www.TrueConf.com